First of all, we need activate the virtual machine(kali linux). After that, we should search tools in kali linux which is theharvest.
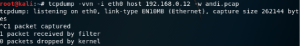
In command line, we should type this:
![]()
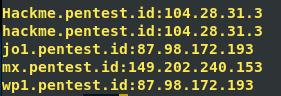
This is for getting the information from pentest.id such as Ip address and DNS record. Like this:
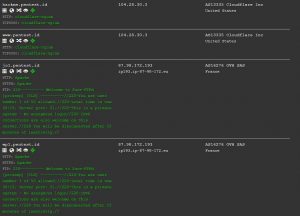
And also, we can check dnsdumpster.com to confirm the DNS record we got from theharvester.
After that, we are using the another tool which is WPScan to emurate the users. In command line we should type this:
![]()
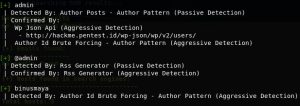
It would appear like this and we found the users which is binusmaya: